Ipset is something different
Go to:
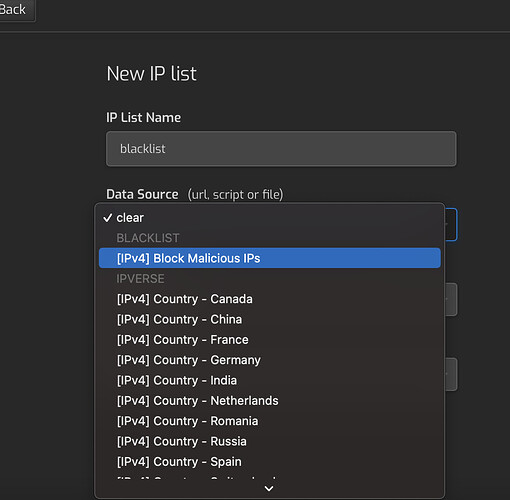
Edit Server (Cogs icon) → Firewall → Manage IP lists → Add Ip list
Then give it a name and select black list
Save
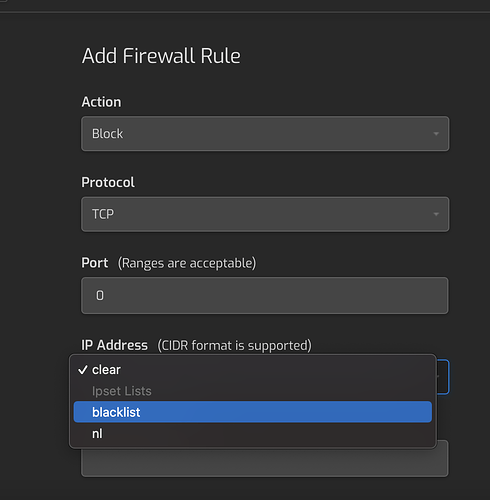
Then go to firewall and add a rule:
Then save the number of attacks should be decreased by a lot is my exceperince…
It still happens but is a lot of less times;
2021-04-20 01:18:54 dovecot_login authenticator failed for (User) [212.70.149.71]: 535 Incorrect authentication data (set_id=abraham@)
2021-04-20 01:18:59 TLS error on connection from (User) [212.70.149.71] (recv): The TLS connection was non-properly terminated.
2021-04-20 01:19:20 dovecot_login authenticator failed for ([31.210.20.155]) [31.210.20.155]: 535 Incorrect authentication data (set_id=egor)
2021-04-20 01:19:28 dovecot_login authenticator failed for ([31.210.20.41]) [31.210.20.41]: 535 Incorrect authentication data (set_id=alan)
2021-04-20 01:20:23 dovecot_login authenticator failed for (User) [141.98.10.235]: 535 Incorrect authentication data (set_id=seng)