Cloudflare as a PITA…under statement. 
Well, I guess I just like hell, as I decided to implement Cloudflare at the same time of migrating everything from VestaCP to HestiaCP. Like I said, I’m having a quick moment of free time finally, so trying to get this all sorted out.
So, I’m unfortunately, also new to Cloudflare, so it seems like I might have made some stupid/simply mistakes. I kept trying to figure out what Eris comment meant.  He’s like yoda, just short tip/direction, and Luke skywalker gotta figure out the rest.
He’s like yoda, just short tip/direction, and Luke skywalker gotta figure out the rest.
Anyway, I figured since pausing cloudflare was the thing that got things working, I figured there must be an issue there. So I’m updating this thread to help anyone else in my situation (new to Hestia and new to Cloudflare). This tip will save you a good few hours (I wish I had my time saved).
I believe the issue was because I had the cname and A records for mail and webmail behind the Cloudflair proxy. I guess most people have their production web site server separate from their email, so the guides don’t always clearly mention this. Anyway, I disabled the proxy option on the DNS records for mail and webmail on all my domains configured through Cloudflare.
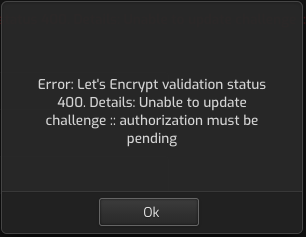
And that worked. What was strange during my testing, was that even with the proxy on, I could still successfully save the SSL Let’s encrypt option on the 1st domain I was troubleshooting. IDK, perhaps it’s because the SSL cert was already loaded, so it did not reach out to Let’s Encrypt servers, and that’s why it appeared to work, but it wouldn’t have. So I think I said myself a headache down the road when the server goes to renew these certificates, as now Cloudflare is properly configured.
So the key take away: ENSURE THAT PROXY is disabled on the INDIVIDUAL CLOUDFLARE DNS entries for webmail and mail. Basically, anything related to mail should have proxy disabled.
For anyone that’s interested, here are the two articles I found related to this:
And also the second domain issue has been resolved. No idea why the hell the DNS took so long to propogate, but perhaps as falzo mentioned, maybe it was just blocking my requests as I had attempted so many times. I’ve been dealing with trying to figure out why the hell gmail is throwing some of my emails into archive (skipping inbox) for no reason (still haven’t figured it out), but that gave me enough time to take a break from this, that by the time I came back and attempted again, the server seemed to have finally figured out where webmail.mydomain.com was.
So all mail servers are now configured with SSL certs. Thanks guys!!!