I’m on Ubuntu 18.04 running HestiaCP Version 1.0.6.
I’ve migrated a domain from a VestaCP running 16.04 Ubuntu, my question is…
Why so many:
dovecot_login authenticator failed for (User) ip-address-here: 535 Incorrect authentication data error on my exim4 main log.
Why fail2ban is not banning those IP addresses.
Based on the log, I think a bot is bruteforcing email login on my server, targeting the domain I just migrated.
Is there anyway to fix this? No banned IP in Fail2ban/Fireall section of HestiaCP.
NOTE: The migrated domain running on the HestiaCP machine is not yet live. The domain still points to the VestaCP server, so just wondering how the have discovered the new server and started brute forcing it.
Just on mobile, but could this be related? https://forum.vestacp.com/viewtopic.php?t=9040#p30273
Can you maybe check it on your side and have a look, if adjust the filters will ban the attacker? If you like, you can also create a pull request with adjusted fail2ban filters.
Hi there! Thank you for responding. I did actually read on that topic, but was hesitant to apply the suggested solution, since I thought HestiaCP had fixed that on their fork.
What seemed to worked for me though, was inserting findtime and maxretry, on the exim and dovecot configs.
When I check on /var/log/fail2ban.log there were banned IPs for exim.
What are your thought on this? Is it problem sovled and should I move on now?
Sorry I asked, I’m not an expert on this, just learning by myself.
Just checked: The filter files arent shipped with hestia itself, it uses the system default. So I don’t know if the issue is resolved, depends if you still have no entry for dovecot attack bans?
HI!
Yeah, have these entries for exim and dovecot. Please see image reference link below.
Image:
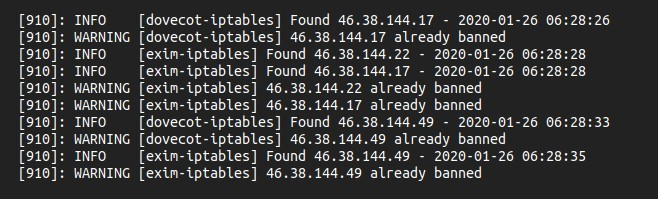
Thanks for responding.
Hmm, can you also post a iptables -L to show the banned ips? Please think about to anonmyze non attacker ip addresses.
I’m sorry, I’m not sure how should I anonymize non attacker IP addresses. There are lots of them and seems like all attackers.
iptables -L output:
https://pastebin.com/MyawvXzs
Looks all is working properly, the attacker got banned in iptables:
1. REJECT all -- 46.38.144.49 anywhere reject-with icmp-port-unreachable
