How can I ban/block an email address so he can’t send me emails?
Is there some kind of blacklist or something similar to manage this?
Thanks in advance
How can I ban/block an email address so he can’t send me emails?
Is there some kind of blacklist or something similar to manage this?
Thanks in advance
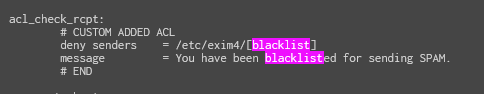
Yes. Edit the file /etc/exim4/exim4.conf.template and:
accept statement of the acl_check_rcpt: block # CUSTOM ADDED ACL
deny senders = /etc/exim4/[FILENAME]
message = You have been blacklisted for sending SPAM.
# END
Replace [FILENAME] with a file that you will need to create, which will contain the email address(es) to block, or the whole domain(s).
systemctl restart exim4.service
Feel free to put whatever you want in the comments (lines starting with #)
I would have to dig, but it should be already implemented. There was a PR…
It would be awesome if there would be UI for Global list management, perhaps in combination with Track delivery reports.
It does not work, I did not receive any mail from any email address
i have created a file named blacklist so but it doesn’t work, i don’t know if i have to put some extension to the file or what is failing
Should be blacklist without the brackets
and the file just name blacklist and inside put mails ?
Yes
Thanks all, working fine the block mail. It would be very interesting to have this option in the same ui.
Thanks all 
I use rspamd on a couple of hestia servers instead of spamassassin. I’ve set it up with a bunch of custom allow / deny lists which can be edited from a web interface. I’ve blocked a few troublesome TLDs such as .icu with great success. Worth looking into if you want to do a lot of this sort of thing.
Rspamd is supposedly faster than Spamassassin. How difficult/easy was the integration and what would you say about performance? Can you now use global and (in combination with) domain-specific lists?
Its honestly not hard, apart from several fiddly exim conf inserts. I was trying to write a script to do it and post in in these forums or submit to the devs, but the exim config alterations probably have to be done manually.
Performance seems good, but where it really shines is the gui interface, where you can monitor what mails are blocked, and change rules on the fly.
I think all rules are globally applied however. i.e. they are applied to all mail entering the server regardless of its destination.
Sounds good, it’s great to have UI to track delivery. Global blocking for a single domain and some .tld’s is fine. For managing multiple domains custom rules are rather important.
This sounds interesting. Do you have any notes somewhere that you would like to share?
So if we could “sed” the changes in the exim conf file it would be trivial.
If I wanted to take back the changes would I have to undo the exim.conf changes too or just uninstall the software?
I thought I’d posted this before, but sure, here’s as far as I got.
#!/bin/bash
# Are we root enough?
## Install Redis as a pre-requisite
# Get an updated version of redis
add-apt-repository -y ppa:chris-lea/redis-server
apt update
apt install -y redis-server redis-tools
# Edit config file
cp /etc/redis/redis.conf /etc/redis/redis.orig
grep -v -e "^#" -e "^;" -e "^$" redis.orig > redis.conf
sed -i 's/^bind .*/bind 127.0.0.1 ::1/' /etc/redis/redis.conf
echo "maxmemory 100mb" >> /etc/redis/redis.conf
echo "maxmemory-policy volatile-ttl" >> /etc/redis/redis.conf
echo 1 > /proc/sys/vm/overcommit_memory
systemctl enable redis-server
systemctl restart redis-server
## Now install rspamd from repos. Ubuntu version way behind.
CODENAME=`lsb_release -c -s`
wget -O- https://rspamd.com/apt-stable/gpg.key | apt-key add -
echo "deb [arch=amd64] http://rspamd.com/apt-stable/ $CODENAME main" > /etc/apt/sources.list.d/rspamd.list
echo "deb-src [arch=amd64] http://rspamd.com/apt-stable/ $CODENAME main" >> /etc/apt/sources.list.d/rspamd.list
apt-get update
apt-get --no-install-recommends install rspamd
# Add config files
cat <<'EOF' > /etc/rspamd/local.d/redis.conf
write_servers = "127.0.0.1:6379";
read_servers = "127.0.0.1:6379";
EOF
cat <<'EOF' > /etc/rspamd/local.d/history_redis.conf
nrows = 1000;
EOF
## Interactively generate password
echo "Generating rspamd admin gui password. Please enter it below"
NEWPASS=$( rspamadm pw )
echo "password = \"${NEWPASS}\";" > /etc/rspamd/local.d/worker-controller.inc
cat <<'EOF' > /etc/rspamd/local.d/options.inc
history_rows = 1000;
EOF
cat <<'EOF' > /etc/rspamd/local.d/multimap.conf
# local.d/multimap.conf
# create the map files in /var/lib/rspamd with _rspamd:_rspamd ownership.
CUSTOM_WHITELIST_DOMAIN {
type = "from";
filter = "email:domain";
map = "/var/lib/rspamd/CUSTOM_whitelist_domain.map";
action = "accept";
description = "Accept if sender is from domains in this list";
}
CUSTOM_BLACKLIST_DOMAIN {
type = "from";
filter = "email:domain";
map = "/var/lib/rspamd/CUSTOM_blacklist_domain.map";
action = "accept";
description = "Hard reject if sender is from domains in this list";
}
CUSTOM_WHITELIST_EMAILADD {
type = "from";
filter = "email";
map = "/var/lib/rspamd/CUSTOM_whitelist_emailadd.map";
score = -5.0
description = "Score -5 if recipient is in this list";
}
CUSTOM_WHITELIST_IP {
type = "ip";
filter = true;
map = "/var/lib/rspamd/CUSTOM_whitelist_ip.map";
action = "accept" ;
description = "Accept if sender IP address is in this list";
}
CUSTOM_BLACKIST_TLD {
type = "from";
filter = "email";
map = "/var/lib/rspamd/CUSTOM_blacklist_tld.map";
regexp = true;
action = "reject";
description = "Reject from .icu domain and friends (regex)";
}
EOF
# Set up Custom multimaps
cat <<'EOF' > /var/lib/rspamd/CUSTOM_blacklist_domain.map
# local blacklist domain map
# Rejects emails from these domains. No further processing
# see /etc/rspamd/local.d/multimap.conf
# Put the whold domain in eg
# example.com
EOF
cat <<'EOF' > /var/lib/rspamd/CUSTOM_blacklist_tld.map
# local blacklist TLD domain map
# Rejects emails from an ENTIRE TLD. No further processing
# see /etc/rspamd/local.d/multimap.conf
# Use a regex with care eg this will block [email protected]
# .+@.+\.xyz$
EOF
cat <<'EOF' > /var/lib/rspamd/CUSTOM_whitelist_domain.map
# local whitelist domain map
# bypasses all checks. Sets score = 0.0
# see /etc/rspamd/local.d/multimap.conf
# Put the whold domain in eg
# example.com
EOF
cat <<'EOF' > /var/lib/rspamd/CUSTOM_whitelist_emailadd.map
# local whitelist email address map
# alters score -5
# see /etc/rspamd/local.d/multimap.conf
# Add whole email addresses. eg
# [email protected]
EOF
cat <<'EOF' > /var/lib/rspamd/CUSTOM_whitelist_ip.map
# local whitelist ip map
# Bypasses scanning, sets score = 0.0
# see /etc/rspamd/local.d/multimap.conf
# Enter whole IP addresses eg
# 200.100.50.88
EOF
chown _rspamd:_rspamd /var/lib/rspamd/CUSTOM*.map
systemctl restart rspamd
## Now change Exim config
# Manual for now
# Disable spamassassin.
#systemctl restart exim4
#systemctl stop spamassassin
#systemctl disable spamassassin
## Change Hestia Config
# Not sure if we need this.
sed -i "s/^ANTISPAM_SYSTEM=.*/ANTISPAM_SYSTEM='rspamd'/" /usr/local/hestia/conf/hestia.conf
# Insert stanza into config to allow access to rspamd gui.
cp /usr/local/hestia/nginx/conf/nginx.conf /usr/local/hestia/nginx/conf/nginx.conf.save
# Manual insert for now
# location /rspamd/ {
# proxy_pass http://localhost:11334/;
# proxy_set_header Host $host;
# proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
# auth_basic "Restricted Content";
# auth_basic_user_file /etc/apache2/admin.passwd;
# }
#
systemctl restart hestia
I’m pretty handy with sed, but I couldn’t really see an easy way to do this. If hestia admins would consider putting some placeholder text in there, that would make it considerably easier.
Basically, if you look at the exim config, you’ll see that the spamassassin config is held in several conditional blocks. For each of those, you have to introduce another conditional block for rspamd eg.
.ifdef SPAMASSASSIN
spamd_address = 127.0.0.1 783
.endif
## add one for rspamd
.ifdef RSPAMD
spamd_address = 127.0.0.1 11333 variant=rspamd
.endif
There are 4 or 5 of these blocks, and some are quite complex. So for the moment, I’ve just been adding them in manually, which takes a couple of minutes once you’ve done it a few times.
As to the other part of your question, as all the config is held in conditional blocks, all you’d have to to do revert is to change the variables at the top of the file. ie.
# SPAMASSASSIN = yes
RSPAMD=yes
OK, final post to detail exim config changes. Only three I notice, as one of them in my config was mirroring a non-standard addition to spamassassin. So:
# Top of file
#SPAMASSASSIN = yes
RSPAMD=yes
# First conditional block
.ifdef RSPAMD
spamd_address = 127.0.0.1 11333 variant=rspamd
.endif
# Second conditional block in acl_check_receipt
.ifdef RSPAMD
warn set acl_m1 = no
warn condition = ${if exists {/etc/exim4/domains/$domain/antispam}{yes}{no}}
set acl_m1 = yes
.endif
# Third conditional block in acl_check_data
.ifdef RSPAMD
accept hosts = +relay_from_hosts
accept condition = ${if eq{$interface_port}{587}}
accept authenticated = *
# If message size is less than 500k and the domain has antispam enabled, scan the message with rspamd
# This will set variables as follows: $spam_action, $spam_score, $spam_score_int (spam score x10), $spam_report, $spam_bar
# So we add these as headers, first removing any existing ones
warn condition = ${if < {$message_size}{1M}}
condition = ${if eq{$acl_m1}{yes}{yes}{no}}
spam = nobody:true
remove_header = x-spam-bar : x-spam-score : x-spam-report : x-spam-status
add_header = X-Spam-Score: $spam_score_int
add_header = X-Spam-Report: $spam_report
add_header = X-Spam-Action: $spam_action
set acl_m2 = $spam_score_int
# add x-spam-bar header if score is positive
warn condition = ${if >{$spam_score_int}{0}}
add_header = X-Spam-Bar: $spam_bar
# use greylisting if action is soft reject
defer message = Please try again later
condition = ${if eq{$spam_action}{soft reject}}
# Hard reject if spam action is reject
deny message = Message discarded as high-probability spam
condition = ${if eq{$spam_action}{reject}}
# add spam-score and spam-report header when "add header" action is recommended by rspamd
warn
condition = ${if eq{$spam_action}{add header}}
add_header = X-Spam-Status: Yes
# Subject Re-write
add_header = X-Spam-Subject: [*SPAMINESS=$spam_score_int*] $h_Subject
message = Detected spam (from $sender_address to $recipients).
# add x-spam-status header if message action is 'rewrite subject'
warn
#! condition = ${if match{$spam_action}{^no action\$|^greylist\$}}
condition = ${if eq{$spam_action}{rewrite subject}}
add_header = X-Spam-Status: Yes
# Subject Re-write
add_header = X-Spam-Subject: [*SPAMINESS=$spam_score_int*] $h_Subject
message = Detected spam (from $sender_address to $recipients).
.endif
Please open an issue about it at Github (or create a new thread with rspamd in the subject).
I’ve also been using Rspamd for the past 3-4 years (but not on HestiaCP) and it is very powerful, even though it is significantly harder to configure than SA, also because it offers many more features.
I have added pluto’s installation and config snippets to