Hi @sahsanu
I am getting the issue with those two domains.
=============================
Date Time: 2024-11-12 05:53:02
WEB_SYSTEM: apache2
PROXY_SYSTEM: nginx
user:
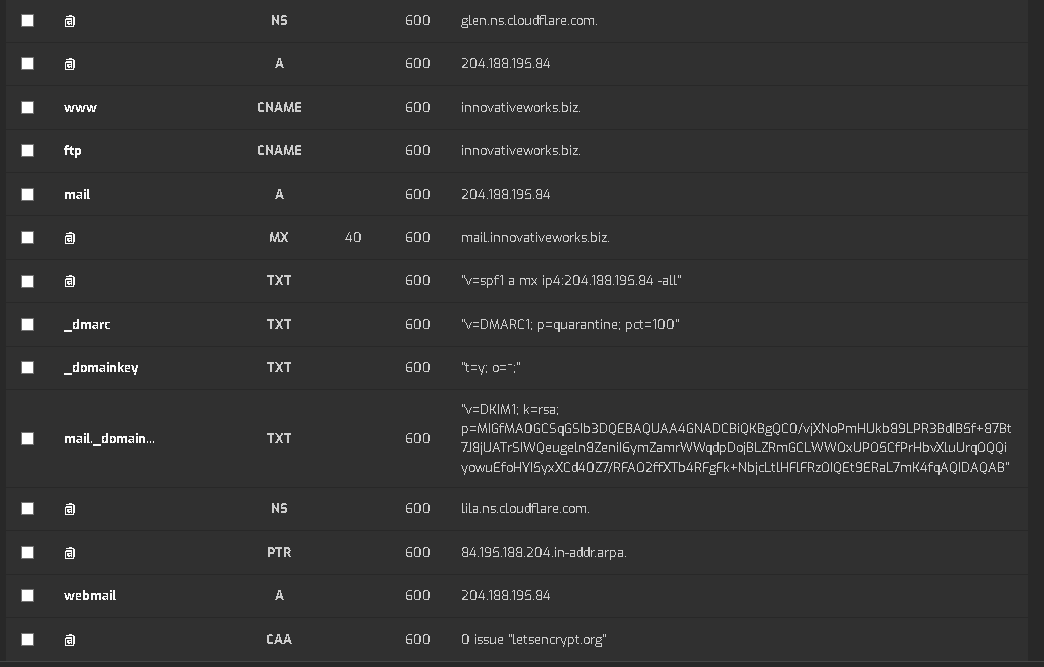
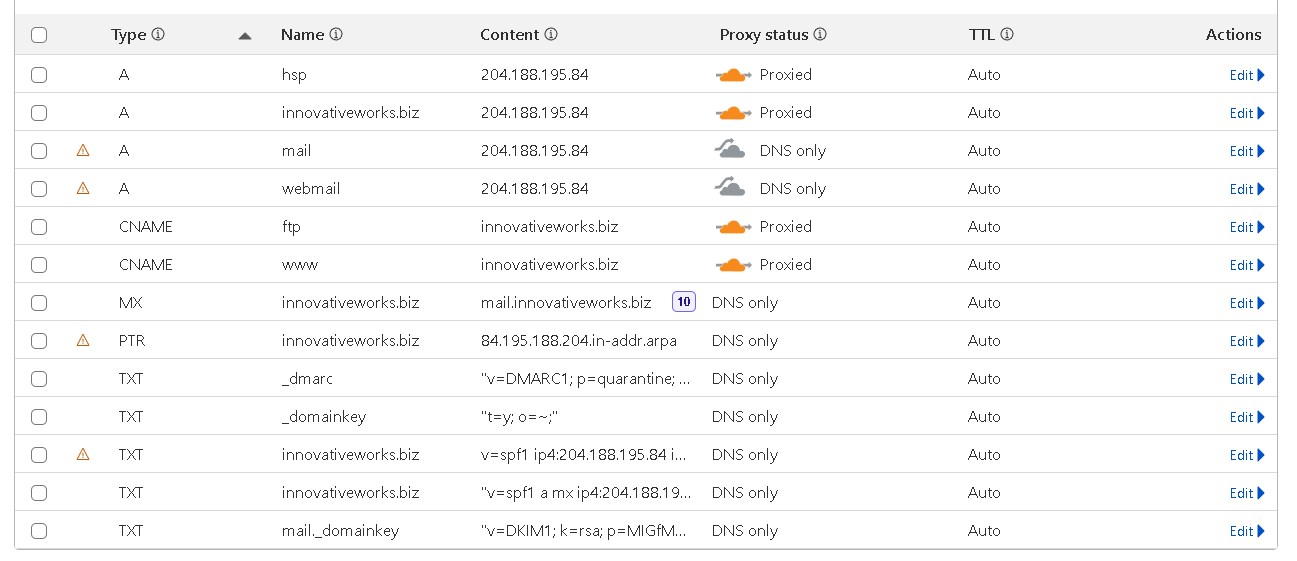
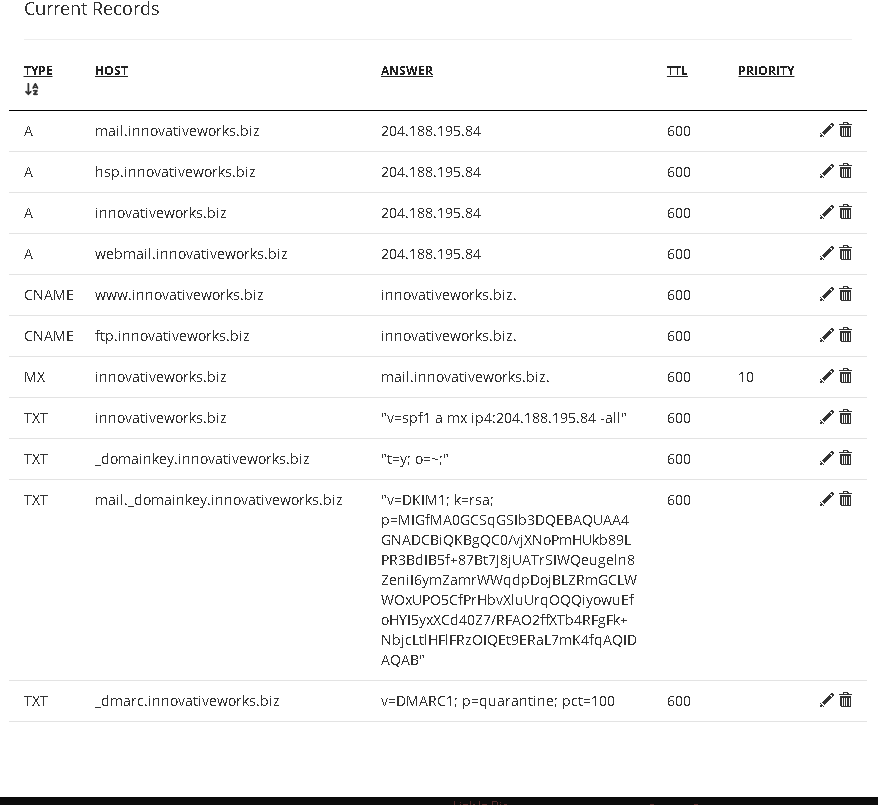
domain: mail.innovativeworks.biz
- aliases: webmail.innovativeworks.biz
- proto: http-01
- wildcard:
==[Step 1]==
- status: 200
- nonce: SEOe4WhpSr3fVw4Cb2kz98dN3DHOyr83baGZLD2kXPoLDm4L3tk
- answer: HTTP/2 200
server: nginx
date: Tue, 12 Nov 2024 11:53:02 GMT
content-type: application/json
content-length: 746
cache-control: public, max-age=0, no-cache
replay-nonce: SEOe4WhpSr3fVw4Cb2kz98dN3DHOyr83baGZLD2kXPoLDm4L3tk
x-frame-options: DENY
strict-transport-security: max-age=604800
==[API call]==
exit status: 0
==[Step 2]==
- status: 201
- nonce: SHEOpopMqlPpgnJnmNuXRp2jS49UBXy5xq-Di3ZNdOMXlC25gGo
- authz: https://acme-v02.api.letsencrypt.org/acme/authz-v3/429075333687
https://acme-v02.api.letsencrypt.org/acme/authz-v3/429075333697
- finalize: https://acme-v02.api.letsencrypt.org/acme/finalize/1707821587/322384711767
- payload: {"identifiers":[{"type":"dns","value":"mail.innovativeworks.biz"},{"type":"dns","value":"webmail.innovativeworks.biz"}]}
- answer: HTTP/2 201
server: nginx
date: Tue, 12 Nov 2024 11:53:03 GMT
content-type: application/json
content-length: 500
boulder-requester: 1707821587
cache-control: public, max-age=0, no-cache
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
location: https://acme-v02.api.letsencrypt.org/acme/order/1707821587/322384711767
replay-nonce: SHEOpopMqlPpgnJnmNuXRp2jS49UBXy5xq-Di3ZNdOMXlC25gGo
x-frame-options: DENY
strict-transport-security: max-age=604800
{
"status": "pending",
"expires": "2024-11-19T11:53:03Z",
"identifiers": [
{
"type": "dns",
"value": "mail.innovativeworks.biz"
},
{
"type": "dns",
"value": "webmail.innovativeworks.biz"
}
],
"authorizations": [
"https://acme-v02.api.letsencrypt.org/acme/authz-v3/429075333687",
"https://acme-v02.api.letsencrypt.org/acme/authz-v3/429075333697"
],
"finalize": "https://acme-v02.api.letsencrypt.org/acme/finalize/1707821587/322384711767"
}
order: https://acme-v02.api.letsencrypt.org/acme/order/1707821587/322384711767
==[API call]==
exit status: 0
==[Step 3]==
- status: 200
- nonce: SHEOpopMp2gmHxohqu6oOv2y9Xh2-pdMWAiG3Ph1Tu8b0GNPI-w
- url: https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333687/fAYG0Q
- token: UU8eoPEEK4F19s5-MURD9Jo3MqJbSBvJAFYmN4yO4Ns
- answer: HTTP/2 200
server: nginx
date: Tue, 12 Nov 2024 11:53:03 GMT
content-type: application/json
content-length: 808
boulder-requester: 1707821587
cache-control: public, max-age=0, no-cache
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
replay-nonce: SHEOpopMp2gmHxohqu6oOv2y9Xh2-pdMWAiG3Ph1Tu8b0GNPI-w
x-frame-options: DENY
strict-transport-security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "mail.innovativeworks.biz"
},
"status": "pending",
"expires": "2024-11-19T11:53:03Z",
"challenges": [
{
"type": "tls-alpn-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333687/ftHObQ",
"status": "pending",
"token": "UU8eoPEEK4F19s5-MURD9Jo3MqJbSBvJAFYmN4yO4Ns"
},
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333687/fAYG0Q",
"status": "pending",
"token": "UU8eoPEEK4F19s5-MURD9Jo3MqJbSBvJAFYmN4yO4Ns"
},
{
"type": "dns-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333687/8n5vVA",
"status": "pending",
"token": "UU8eoPEEK4F19s5-MURD9Jo3MqJbSBvJAFYmN4yO4Ns"
}
]
}
==[API call]==
exit status: 0
==[Step 5]==
- status: 200
- url: https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333687/fAYG0Q
- nonce: SEOe4WhphmprhWc1axPuo0HnUSlOxLZoTJQ5YKab4oJurqGAzXU
- validation: https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333687/fAYG0Q
- details:
- answer: HTTP/2 200
server: nginx
date: Tue, 12 Nov 2024 11:53:09 GMT
content-type: application/json
content-length: 187
boulder-requester: 1707821587
cache-control: public, max-age=0, no-cache
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
link: <https://acme-v02.api.letsencrypt.org/acme/authz-v3/429075333687>;rel="up"
location: https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333687/fAYG0Q
replay-nonce: SEOe4WhphmprhWc1axPuo0HnUSlOxLZoTJQ5YKab4oJurqGAzXU
x-frame-options: DENY
strict-transport-security: max-age=604800
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333687/fAYG0Q",
"status": "pending",
"token": "UU8eoPEEK4F19s5-MURD9Jo3MqJbSBvJAFYmN4yO4Ns"
}
==[API call]==
exit status: 0
==[Step 3]==
- status: 200
- nonce: SEOe4WhpCRWivP_wW4bmY54_rub715Nii6-bvMf19RQj4Kh3XwE
- url: https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333697/SsDBgQ
- token: MNPk5MSXwCuJRU6TRICy3dG0OjWNgiAa2vpUtXBlpGs
- answer: HTTP/2 200
server: nginx
date: Tue, 12 Nov 2024 11:53:13 GMT
content-type: application/json
content-length: 811
boulder-requester: 1707821587
cache-control: public, max-age=0, no-cache
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
replay-nonce: SEOe4WhpCRWivP_wW4bmY54_rub715Nii6-bvMf19RQj4Kh3XwE
x-frame-options: DENY
strict-transport-security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "webmail.innovativeworks.biz"
},
"status": "pending",
"expires": "2024-11-19T11:53:03Z",
"challenges": [
{
"type": "tls-alpn-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333697/XsDfLg",
"status": "pending",
"token": "MNPk5MSXwCuJRU6TRICy3dG0OjWNgiAa2vpUtXBlpGs"
},
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333697/SsDBgQ",
"status": "pending",
"token": "MNPk5MSXwCuJRU6TRICy3dG0OjWNgiAa2vpUtXBlpGs"
},
{
"type": "dns-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333697/mw_HrQ",
"status": "pending",
"token": "MNPk5MSXwCuJRU6TRICy3dG0OjWNgiAa2vpUtXBlpGs"
}
]
}
==[API call]==
exit status: 0
==[Step 5]==
- status: 200
- url: https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333697/SsDBgQ
- nonce: SEOe4Whpf0N_dMpfmL1p_sgjZCeBkFOtQppoJTsKZI7-FA9wh0o
- validation: https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333697/SsDBgQ
- details:
- answer: HTTP/2 200
server: nginx
date: Tue, 12 Nov 2024 11:53:18 GMT
content-type: application/json
content-length: 187
boulder-requester: 1707821587
cache-control: public, max-age=0, no-cache
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
link: <https://acme-v02.api.letsencrypt.org/acme/authz-v3/429075333697>;rel="up"
location: https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333697/SsDBgQ
replay-nonce: SEOe4Whpf0N_dMpfmL1p_sgjZCeBkFOtQppoJTsKZI7-FA9wh0o
x-frame-options: DENY
strict-transport-security: max-age=604800
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/429075333697/SsDBgQ",
"status": "pending",
"token": "MNPk5MSXwCuJRU6TRICy3dG0OjWNgiAa2vpUtXBlpGs"
}
==[API call]==
exit status: 0
==[Step 6]==
- status: 403
- nonce: SHEOpopMF2pGpEk6FDj_jp6mikfJ2eekXHzyV1Que5RylNJ7ezo
- payload: {"csr":"MIIFQjCCAyoCAQAwgakxLDAqBgkqhkiG9w0BCQEWHWluZm9AbWFpbC5pbm5vdmF0aXZld29ya3MuYml6MQswCQYDVQQGEwJVUzETMBEGA1UECAwKQ2FsaWZvcm5pYTEWMBQGA1UEBwwNU2FuIEZyYW5jaXNjbzEPMA0GA1UECgwGSGVzdGlhMQswCQYDVQQLDAJJVDEhMB8GA1UEAwwYbWFpbC5pbm5vdmF0aXZld29ya3MuYml6MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAu2HrqNacjcwJlIyWgjW5p1MZyrvcjj5kiNE5jyLYTJm_IARzV1cgjMC8wGySPzRSiqctf8694LU7a3tStVCcN-3A5VmW0VbxJWabbxxFtPBJl84va47j5t0RmNvlApbRV8ZlQUDwuM1ZcDMgpv8_K6RoRsUdr9ao-XWnHkpziKFvccREI69x9vR25QfmTmuPLcu78HRM6SC1AfG85IPKHRcEm8rZoziT9bCiWXyEuuBRmSNPeNeGqZCI_m7_Tqq03ld0OZLpBCXBltWBe3txUSmkpf7amEzGiOd2oBmx7hELu4Dme-49-yAU8C3KlfXX0ukiYg8AhGKgFsZefZFv2Nn0xixCBAFfk9NOjffwVo01otKC_Mi8Cz7OnhBGGGWKWNBWChQNGzWEdg560q5yiJsXBSRP08Ecp8v9-ny_mGX1vQT4wg7LfY4vkO9qtTijno3N2Bb8K34XiGecga433PW9Hae7HaFhBRsuennGRJU6vw_X5FrMz_1Mgfsb4sLWZ4CYzCveka5T-o7i9aLKARzL9CRXYd3rrYoIYxxUveaOVb3wzuUt_rxCiFu8wYcqZ1wMdJ0JP_vNHx93SMRZBN2CX2S_NPwVvIV5BnkauvMJBUNIiUEB_OJXH_-flxEHm3SAf9XjFpQPGW7qP-UGHWa1GkueSx2bOPwOvVNWT3ECAwEAAaBTMFEGCSqGSIb3DQEJDjFEMEIwQAYDVR0RBDkwN4IYbWFpbC5pbm5vdmF0aXZld29ya3MuYml6ght3ZWJtYWlsLmlubm92YXRpdmV3b3Jrcy5iaXowDQYJKoZIhvcNAQELBQADggIBAFq0ecbCOLGYhpYnU4LJW7kjK5TEGBPjjoCZLEc8-No8668E5e_D4oHfzMTl-LPS2LRSq8fAWE6r-_IdvKZLslpmP8VENxVxm2XPe_i7tU-eKs4ZjpANbEMIOBH39IQZQC8rrbOy6IqJbMV2o9FyKofXzIQ1YATT1OUBmKE3FB1e9xVkQhaTR468uraMWEJdt0RxAXbuQg5yiF0guwxfcttZaDQsAh6LDSvOokuapgyQ93y-F0oixnprQ0iVnojj4t_2PBeYUk1hENKQL1PxZM4CClJiXHR8cIPLY7he3p3B2AkfXPVfzRM3O0V_WSLhClezI0WS1JezWlzD3hXCQEr8JiDqSkJBjRq-n47iA6KAsrYnfOY4RQHj7M6isq855HSoRm96f-YoNCPRpipRPv7I3N-5chCLj6t9rwJzOJ1_vumJ7Y-Hx4gj-M73jM8tH_KoPFn96FKVXz9HVsEdIrIZvX3i0RipDqJ7Hc0louv03JBSSKrakeLQ7Y-5m1mi8DgUqcEvYRFgDt4l36wj8xc3Nm4J_MAzohkK6NPjjo5AoxW7i4Crj9zqLB77DmpEafy4l0TVJ4bxzBLmiiDXdWRlgxZlcc4n165TJcEkURLE5H0GB2tTh964e1M-_4S2vfjwUZgeAbrQN7sOFLZsx2CmEUdTVRmtJvO6lvm3WuB5"}
- certificate:
- answer: HTTP/2 403
server: nginx
date: Tue, 12 Nov 2024 11:53:25 GMT
content-type: application/problem+json
content-length: 152
boulder-requester: 1707821587
cache-control: public, max-age=0, no-cache
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
replay-nonce: SHEOpopMF2pGpEk6FDj_jp6mikfJ2eekXHzyV1Que5RylNJ7ezo
{
"type": "urn:ietf:params:acme:error:orderNotReady",
"detail": "Order's status (\"pending\") is not acceptable for finalization",
"status": 403
}