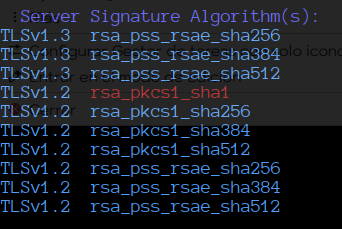
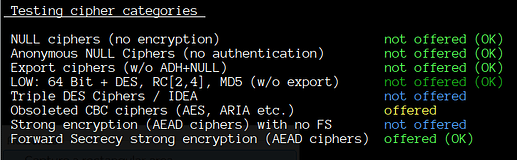
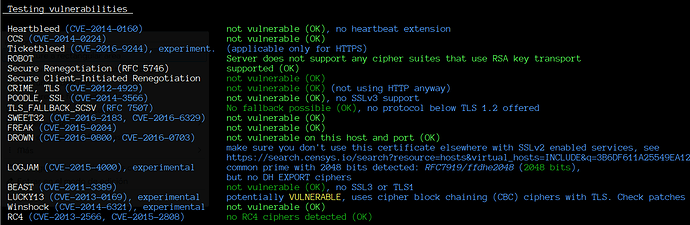
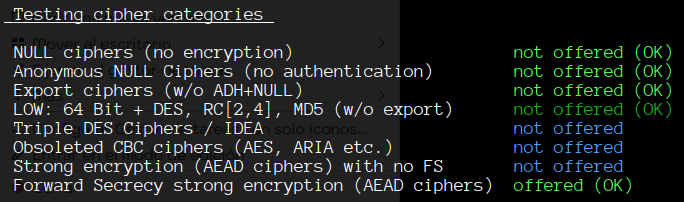
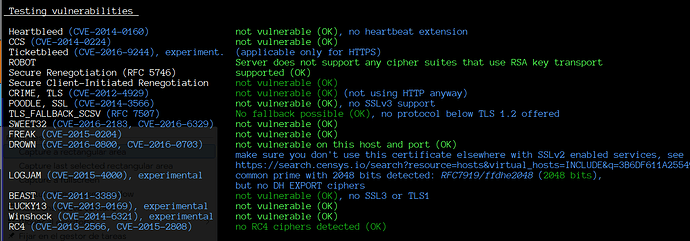
As part of our ongoing efforts to enhance security, it has come to our attention that certain cipher suites used for encryption in Exim may be considered weak and vulnerable to security threats. To mitigate these risks, we are seeking guidance on how to effectively exclude these weak cipher suites from our server’s configuration.
Specifically, we are looking to disable the following weak cipher suites:
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1)
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1)
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (dh 2048)
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (dh 2048)
TLS_DHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (dh 2048)
TLS_DHE_RSA_WITH_AES_128_CCM (dh 2048)
TLS_DHE_RSA_WITH_AES_256_CCM (dh 2048)
TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 2048)
TLS_DHE_RSA_WITH_AES_256_CBC_SHA (dh 2048)
Could you please provide instructions or guidelines on how to achieve this in our Exim server configuration? Any insights or recommendations you can offer would be greatly appreciated.
Thank you for your attention to this matter.