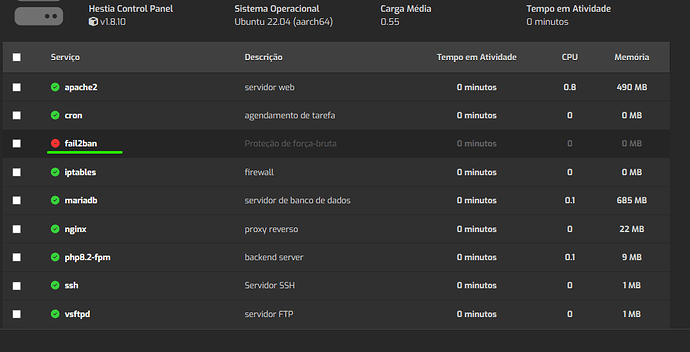
My server was normal, from yesterday to today I simply see the fail2ban service off, can anyone give me any tips? No changes!
As I noticed many attempts on ssh, I decided to change the port now, but the service fail2ban was already down
root@server:~# cat /var/log/fail2ban.log
2023-10-28 23:19:37,673 fail2ban.server [29478]: INFO --------------- -----------------------------------
2023-10-28 23:19:37,673 fail2ban.server [29478]: INFO Starting Fail2b an v0.11.2
2023-10-28 23:19:37,673 fail2ban.observer [29478]: INFO Observer start. ..
2023-10-28 23:19:37,676 fail2ban.database [29478]: INFO Connected to fa il2ban persistent database '/var/lib/fail2ban/fail2ban.sqlite3'
2023-10-28 23:19:37,679 fail2ban.database [29478]: WARNING New database cr eated. Version '4'
2023-10-28 23:19:37,679 fail2ban.jail [29478]: INFO Creating new ja il 'recidive'
2023-10-28 23:19:37,688 fail2ban.jail [29478]: INFO Jail 'recidive' uses pyinotify {}
2023-10-28 23:19:37,691 fail2ban.jail [29478]: INFO Initiated 'pyin otify' backend
2023-10-28 23:19:37,695 fail2ban.filter [29478]: INFO maxRetry: 5
2023-10-28 23:19:37,695 fail2ban.filter [29478]: INFO findtime: 864 00
2023-10-28 23:19:37,695 fail2ban.actions [29478]: INFO banTime: 8640 00
2023-10-28 23:19:37,695 fail2ban.filter [29478]: INFO encoding: UTF -8
2023-10-28 23:19:37,695 fail2ban.filter [29478]: INFO Added logfile: '/var/log/fail2ban.log' (pos = 0, hash = 6c1ad902477371361e0f743ef98b60129c3a970 6)
2023-10-28 23:19:37,695 fail2ban.jail [29478]: INFO Creating new ja il 'ssh-iptables'
2023-10-28 23:19:37,695 fail2ban.jail [29478]: INFO Jail 'ssh-iptab les' uses pyinotify {}
2023-10-28 23:19:37,697 fail2ban.jail [29478]: INFO Initiated 'pyin otify' backend
2023-10-28 23:20:49,463 fail2ban.jail [883]: INFO Creating new jail 'ssh-iptables'
2023-10-28 23:20:49,463 fail2ban.jail [883]: INFO Jail 'ssh-iptable s' uses pyinotify {}
2023-10-28 23:20:49,465 fail2ban.jail [883]: INFO Initiated 'pyinot ify' backend
2023-10-28 23:20:49,465 fail2ban.filter [883]: INFO maxLines: 1
2023-10-28 23:20:49,482 fail2ban.filter [883]: INFO maxRetry: 5
2023-10-28 23:20:49,482 fail2ban.filter [883]: INFO findtime: 600
2023-10-28 23:20:49,482 fail2ban.actions [883]: INFO banTime: 600
2023-10-28 23:20:49,482 fail2ban.filter [883]: INFO encoding: UTF-8
2023-10-28 23:20:49,484 fail2ban.filter [883]: INFO Added logfile: '/ var/log/auth.log' (pos = 16254, hash = 21a4e6cf7466b96d0185a95d0c924ecdf27f2977)
2023-10-28 23:20:49,484 fail2ban.jail [883]: INFO Creating new jail 'vsftpd-iptables'
2023-10-28 23:20:49,484 fail2ban.jail [883]: INFO Jail 'vsftpd-ipta bles' uses pyinotify {}
2023-10-28 23:20:49,488 fail2ban.jail [883]: INFO Initiated 'pyinot ify' backend
2023-10-28 23:20:49,489 fail2ban.filter [883]: INFO maxRetry: 5
2023-10-28 23:20:49,490 fail2ban.filter [883]: INFO findtime: 600
2023-10-28 23:20:49,490 fail2ban.actions [883]: INFO banTime: 600
2023-10-28 23:20:49,490 fail2ban.filter [883]: INFO encoding: UTF-8
2023-10-28 23:20:49,490 fail2ban.filter [883]: INFO Added logfile: '/ var/log/vsftpd.log' (pos = 0, hash = da39a3ee5e6b4b0d3255bfef95601890afd80709)
2023-10-28 23:20:49,490 fail2ban.jail [883]: INFO Creating new jail 'exim-iptables'
2023-10-28 23:20:49,490 fail2ban.jail [883]: INFO Jail 'exim-iptabl es' uses pyinotify {}
2023-10-28 23:20:49,492 fail2ban.jail [883]: INFO Initiated 'pyinot ify' backend
2023-10-28 23:20:49,502 fail2ban.filter [883]: INFO maxRetry: 5
2023-10-28 23:20:49,502 fail2ban.filter [883]: INFO findtime: 600
2023-10-28 23:20:49,502 fail2ban.actions [883]: INFO banTime: 600
2023-10-28 23:20:49,502 fail2ban.filter [883]: INFO encoding: UTF-8
2023-10-28 23:20:49,503 fail2ban.filter [883]: INFO Added logfile: '/ var/log/exim4/mainlog' (pos = 414, hash = 930d84adae47b74863aa525df15fad90aa2f54 e5)
2023-10-29 10:56:03,329 fail2ban.jail [883]: INFO Jail 'recidive' s topped
2023-10-29 10:56:03,330 fail2ban.jail [883]: INFO Jail 'ssh-iptable s' stopped
2023-10-29 10:56:03,331 fail2ban.jail [883]: INFO Jail 'vsftpd-ipta bles' stopped
2023-10-29 10:56:03,331 fail2ban.jail [883]: INFO Jail 'exim-iptabl es' stopped
2023-10-29 10:56:03,331 fail2ban.jail [883]: INFO Jail 'dovecot-ipt ables' stopped
2023-10-29 10:56:03,331 fail2ban.jail [883]: INFO Jail 'hestia-ipta bles' stopped
2023-10-29 10:56:03,331 fail2ban.jail [883]: INFO Jail 'phpmyadmin- auth' stopped
2023-10-29 10:56:03,331 fail2ban.database [883]: INFO Connection to dat abase closed.
2023-10-29 10:56:03,332 fail2ban.server [883]: INFO Exiting Fail2ban
2023-10-29 10:56:20,159 fail2ban.server [891]: INFO ----------------- ---------------------------------
2023-10-29 10:56:20,160 fail2ban.server [891]: INFO Starting Fail2ban v0.11.2
2023-10-29 10:56:20,160 fail2ban.observer [891]: INFO Observer start...
2023-10-29 10:56:20,218 fail2ban.database [891]: INFO Connected to fail 2ban persistent database '/var/lib/fail2ban/fail2ban.sqlite3'
2023-10-29 10:56:20,220 fail2ban.jail [891]: INFO Creating new jail 'recidive'
2023-10-29 10:56:20,561 fail2ban.jail [891]: INFO Jail 'recidive' u ses pyinotify {}
2023-10-29 10:56:20,564 fail2ban.jail [891]: INFO Initiated 'pyinot ify' backend
2023-10-29 10:56:20,568 fail2ban.filter [891]: INFO maxRetry: 5
2023-10-29 10:56:20,568 fail2ban.filter [891]: INFO findtime: 86400
2023-10-29 10:56:20,568 fail2ban.actions [891]: INFO banTime: 864000
2023-10-29 10:56:20,568 fail2ban.filter [891]: INFO encoding: UTF-8
2023-10-29 10:56:20,569 fail2ban.filter [891]: INFO Added logfile: '/ var/log/fail2ban.log' (pos = 32664, hash = 6c1ad902477371361e0f743ef98b60129c3a9 706)
2023-10-29 10:56:20,569 fail2ban.jail [891]: INFO Creating new jail 'ssh-iptables'
2023-10-29 10:56:20,569 fail2ban.jail [891]: INFO Jail 'ssh-iptable s' uses pyinotify {}
2023-10-29 10:56:20,571 fail2ban.jail [891]: INFO Initiated 'pyinot ify' backend
2023-10-29 10:56:20,572 fail2ban.filter [891]: INFO maxLines: 1
2023-10-29 10:56:20,584 fail2ban.filter [891]: INFO maxRetry: 5
2023-10-29 10:56:20,584 fail2ban.filter [891]: INFO findtime: 600
2023-10-29 10:56:20,584 fail2ban.actions [891]: INFO banTime: 600
2023-10-29 10:56:20,584 fail2ban.filter [891]: INFO encoding: UTF-8
2023-10-29 10:56:20,585 fail2ban.filter [891]: INFO Added logfile: '/ var/log/auth.log' (pos = 926545, hash = 21a4e6cf7466b96d0185a95d0c924ecdf27f2977 )
2023-10-29 10:56:20,585 fail2ban.jail [891]: INFO Creating new jail 'vsftpd-iptables'
2023-10-29 10:56:20,585 fail2ban.jail [891]: INFO Jail 'vsftpd-ipta bles' uses pyinotify {}
2023-10-29 10:56:20,587 fail2ban.jail [891]: INFO Initiated 'pyinot ify' backend
2023-10-29 10:56:20,588 fail2ban.filter [891]: INFO maxRetry: 5
2023-10-29 10:56:20,589 fail2ban.filter [891]: INFO findtime: 600
2023-10-29 10:56:20,589 fail2ban.actions [891]: INFO banTime: 600
2023-10-29 10:56:20,589 fail2ban.filter [891]: INFO encoding: UTF-8
2023-10-29 10:56:20,589 fail2ban.filter [891]: INFO Added logfile: '/ var/log/vsftpd.log' (pos = 3785, hash = bdbd1fd9aca52f0ac86ed1fdffdf09fc4296e8b9 )
2023-10-29 10:56:20,590 fail2ban.jail [891]: INFO Creating new jail 'exim-iptables'
2023-10-29 10:56:20,590 fail2ban.jail [891]: INFO Jail 'exim-iptabl es' uses pyinotify {}
2023-10-29 10:56:20,592 fail2ban.jail [891]: INFO Initiated 'pyinot ify' backend
2023-10-29 10:56:20,598 fail2ban.filter [891]: INFO maxRetry: 5
2023-10-29 10:56:20,598 fail2ban.filter [891]: INFO findtime: 600
2023-10-29 10:56:20,598 fail2ban.actions [891]: INFO banTime: 600
2023-10-29 10:56:20,598 fail2ban.filter [891]: INFO encoding: UTF-8
2023-10-29 10:56:20,599 fail2ban.filter [891]: INFO Added logfile: '/ var/log/exim4/mainlog' (pos = 42201, hash = 930d84adae47b74863aa525df15fad90aa2f 54e5)
2023-10-29 10:56:20,599 fail2ban.jail [891]: INFO Creating new jail 'dovecot-iptables'
2023-10-29 10:56:20,599 fail2ban.jail [891]: INFO Jail 'dovecot-ipt ables' uses pyinotify {}
2023-10-29 10:56:20,601 fail2ban.jail [891]: INFO Initiated 'pyinot ify' backend
2023-10-29 10:56:20,604 fail2ban.datedetector [891]: INFO date pattern `' '`: `{^LN-BEG}TAI64N`
2023-10-29 10:56:20,605 fail2ban.filter [891]: INFO maxRetry: 5
2023-10-29 10:56:20,605 fail2ban.filter [891]: INFO findtime: 600
2023-10-29 10:56:20,605 fail2ban.actions [891]: INFO banTime: 600
2023-10-29 10:56:20,605 fail2ban.filter [891]: INFO encoding: UTF-8
2023-10-29 10:56:20,695 fail2ban.filter [891]: INFO Added logfile: '/ var/log/dovecot.log' (pos = 25054, hash = 284729135b85c18a33d90187c3c42c2a851ec7 b0)
2023-10-29 10:56:20,696 fail2ban.jail [891]: INFO Creating new jail 'hestia-iptables'
2023-10-29 10:56:20,696 fail2ban.jail [891]: INFO Jail 'hestia-ipta bles' uses pyinotify {}
2023-10-29 10:56:20,698 fail2ban.jail [891]: INFO Initiated 'pyinot ify' backend
2023-10-29 10:56:20,699 fail2ban.filter [891]: INFO maxRetry: 5
2023-10-29 10:56:20,699 fail2ban.filter [891]: INFO findtime: 600
2023-10-29 10:56:20,699 fail2ban.actions [891]: INFO banTime: 600
2023-10-29 10:56:20,699 fail2ban.filter [891]: INFO encoding: UTF-8
2023-10-29 10:56:20,699 fail2ban.filter [891]: INFO Added logfile: '/ var/log/hestia/auth.log' (pos = 959, hash = 23baa3bc8d702fb41b36500c8e9d90674f7c 3d75)
2023-10-29 10:56:20,700 fail2ban.jail [891]: INFO Creating new jail 'phpmyadmin-auth'
2023-10-29 10:56:20,700 fail2ban.jail [891]: INFO Jail 'phpmyadmin- auth' uses pyinotify {}
2023-10-29 10:56:20,702 fail2ban.jail [891]: INFO Initiated 'pyinot ify' backend
2023-10-29 10:56:20,703 fail2ban.filter [891]: INFO maxRetry: 5
2023-10-29 10:56:20,703 fail2ban.filter [891]: INFO findtime: 600
2023-10-29 10:56:20,703 fail2ban.actions [891]: INFO banTime: 600
2023-10-29 10:56:20,703 fail2ban.filter [891]: INFO encoding: UTF-8
2023-10-29 10:56:20,703 fail2ban.filter [891]: INFO Added logfile: '/ var/log/auth.log' (pos = 926545, hash = 21a4e6cf7466b96d0185a95d0c924ecdf27f2977 )
2023-10-29 10:56:20,706 fail2ban.jail [891]: INFO Jail 'recidive' s tarted
2023-10-29 10:56:20,709 fail2ban.jail [891]: INFO Jail 'ssh-iptable s' started
2023-10-29 10:56:20,712 fail2ban.jail [891]: INFO Jail 'vsftpd-ipta bles' started
2023-10-29 10:56:20,713 fail2ban.jail [891]: INFO Jail 'exim-iptabl es' started
2023-10-29 10:56:20,714 fail2ban.jail [891]: INFO Jail 'dovecot-ipt ables' started
2023-10-29 10:56:20,716 fail2ban.jail [891]: INFO Jail 'hestia-ipta bles' started
2023-10-29 10:56:20,718 fail2ban.jail [891]: INFO Jail 'phpmyadmin- auth' started
2023-10-29 10:57:17,364 fail2ban.filter [891]: INFO [ssh-iptables] Fo und 159.65.159.167 - 2023-10-29 10:57:17
2023-10-29 10:58:27,056 fail2ban.filter [891]: INFO [ssh-iptables] Fo und 206.189.201.141 - 2023-10-29 10:58:27
2023-10-29 11:03:44,387 fail2ban.filter [891]: INFO [ssh-iptables] Fo und 206.189.201.141 - 2023-10-29 11:03:44
2023-10-29 11:08:18,174 fail2ban.filter [891]: INFO [ssh-iptables] Fo und 159.65.159.167 - 2023-10-29 11:08:18
2023-10-29 11:09:19,642 fail2ban.filter [891]: INFO [ssh-iptables] Fo und 206.189.201.141 - 2023-10-29 11:09:19
2023-10-29 11:13:47,546 fail2ban.filter [891]: INFO [ssh-iptables] Fo und 159.65.159.167 - 2023-10-29 11:13:47
2023-10-29 11:14:36,022 fail2ban.filter [891]: INFO [ssh-iptables] Fo und 206.189.201.141 - 2023-10-29 11:14:35
2023-10-29 11:20:01,938 fail2ban.filter [891]: INFO [ssh-iptables] Fo und 206.189.201.141 - 2023-10-29 11:20:01
2023-10-30 12:14:06,323 fail2ban.actions [891]: NOTICE [ssh-iptables] Ba n 185.224.128.160
2023-10-30 12:14:06,327 fail2ban.filter [891]: INFO [recidive] Found 185.224.128.160 - 2023-10-30 12:14:06
2023-10-30 12:16:09,124 fail2ban.filter [891]: INFO [ssh-iptables] Fo und 104.248.156.219 - 2023-10-30 12:16:08
2023-10-30 12:21:46,730 fail2ban.filter [891]: INFO [ssh-iptables] Fo und 104.248.156.219 - 2023-10-30 12:21:46
2023-10-30 12:24:05,169 fail2ban.actions [891]: NOTICE [ssh-iptables] Un ban 185.224.128.160
2023-10-30 12:27:22,846 fail2ban.filter [891]: INFO [ssh-iptables] Fo und 104.248.156.219 - 2023-10-30 12:27:22
2023-10-30 12:33:03,846 fail2ban.filter [891]: INFO [ssh-iptables] Fo und 104.248.156.219 - 2023-10-30 12:33:03
2023-10-30 12:38:40,604 fail2ban.filter [891]: INFO [ssh-iptables] Fo und 104.248.156.219 - 2023-10-30 12:38:40
2023-10-30 17:08:06,136 fail2ban.server [891]: INFO Shutdown in progr ess...
2023-10-30 17:08:06,137 fail2ban.observer [891]: INFO Observer stop ... try to end queue 5 seconds
2023-10-30 17:08:06,157 fail2ban.observer [891]: INFO Observer stopped, 0 events remaining.
2023-10-30 17:08:06,198 fail2ban.server [891]: INFO Stopping all jail s
2023-10-30 17:08:06,199 fail2ban.filter [891]: ERROR Unable to get fai lures in /var/log/fail2ban.log
2023-10-30 17:08:06,199 fail2ban.filter [891]: ERROR Unable to get fai lures in /var/log/fail2ban.log
2023-10-30 17:08:06,199 fail2ban.filter [891]: ERROR Unable to get fai lures in /var/log/fail2ban.log
2023-10-30 17:08:06,200 fail2ban.filter [891]: ERROR Unable to get fai lures in /var/log/fail2ban.log
2023-10-30 17:08:06,200 fail2ban.filter [891]: ERROR Unable to get fai lures in /var/log/fail2ban.log
2023-10-30 17:08:06,200 fail2ban.filter [891]: ERROR Unable to get fai lures in /var/log/fail2ban.log
2023-10-30 17:08:06,200 fail2ban.filter [891]: ERROR Unable to get fai lures in /var/log/fail2ban.log
2023-10-30 17:08:06,200 fail2ban.filter [891]: ERROR Unable to get fai lures in /var/log/fail2ban.log
2023-10-30 17:08:06,200 fail2ban.filter [891]: ERROR Unable to get fai lures in /var/log/fail2ban.log
2023-10-30 17:08:06,200 fail2ban.filter [891]: INFO Removed logfile: '/var/log/fail2ban.log'
2023-10-30 17:08:06,200 fail2ban.filter [891]: ERROR Unable to get fai lures in /var/log/fail2ban.log
2023-10-30 17:08:06,201 fail2ban.filter [891]: INFO Removed logfile: '/var/log/auth.log'
2023-10-30 17:08:06,201 fail2ban.filter [891]: INFO Removed logfile: '/var/log/vsftpd.log'
2023-10-30 17:08:06,201 fail2ban.filter [891]: INFO Removed logfile: '/var/log/exim4/mainlog'
2023-10-30 17:08:06,221 fail2ban.filter [891]: INFO Removed logfile: '/var/log/dovecot.log'
2023-10-30 17:08:06,237 fail2ban.filter [891]: INFO Removed logfile: '/var/log/hestia/auth.log'
2023-10-30 17:08:06,259 fail2ban.filter [891]: INFO Removed logfile: '/var/log/auth.log'
2023-10-30 17:08:06,324 fail2ban.jail [891]: INFO Jail 'recidive' s topped
2023-10-30 17:08:06,527 fail2ban.jail [891]: INFO Jail 'ssh-iptable s' stopped
2023-10-30 17:08:06,683 fail2ban.jail [891]: INFO Jail 'vsftpd-ipta bles' stopped
2023-10-30 17:08:06,686 fail2ban.jail [891]: INFO Jail 'exim-iptabl es' stopped
2023-10-30 17:08:06,717 fail2ban.jail [891]: INFO Jail 'dovecot-ipt ables' stopped
2023-10-30 17:08:06,718 fail2ban.jail [891]: INFO Jail 'hestia-ipta bles' stopped
2023-10-30 17:08:07,319 fail2ban.jail [891]: INFO Jail 'phpmyadmin- auth' stopped
2023-10-30 17:08:07,320 fail2ban.database [891]: INFO Connection to dat abase closed.
2023-10-30 17:08:07,320 fail2ban.server [891]: INFO Exiting Fail2ban
root@server:~#