Hello Marcus,
Let me go through your misunderstanding one by one:
-
Nowhere in my message I have mentioned that the concept of subdomain.DynDNS will protect the entire server and all the ports. The list and methods of hacking a system, which you describe above, is then not relevant because the solution triggers only on ONE SPECIFIC PORT BOUND TO ONE SPECIFIC IP ADDRESS!
-
The concept of subdomain.DynDNS has nothing to do with DynDNS.com. The abbreviation simply means that it is a dynamic ip address. Because you assumed that it correlates to services offered by a company, you mention about the CNAME. CNAME has nothing to do with the idea of binding a port with an ip address.
-
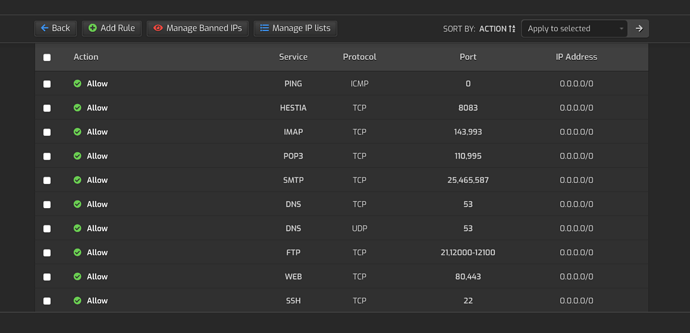
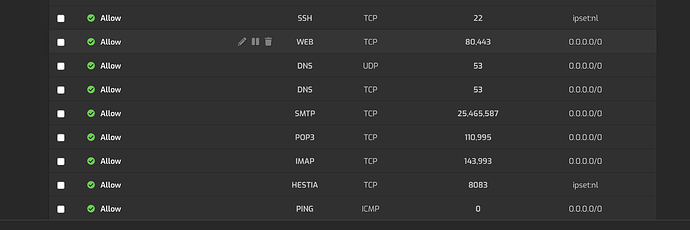
If I configure - with my concept - each port opened by any service, for e.g. 80, 443, 993, 995, 3306, etc. and bind these services to one dynamic ip address (subdomain.DynDNS), then a possibility to hack that service becomes null, unless the kernel is hacked. For a hacker with a different ip address, the kernel declares that secured port to be closed.
In fact, I use dovecot, sshd, webmin, hestia, vsftp, etc. EXCLUSIVELY on specific ports opened to allow traffic to the router ip address (subdomain.DynDNS) that changes dynamically as well as the cluster servers. I myself can access my emails from my router ip address only. Outside, I can access using roundcube under a specific subdomain protected with .htaccess.
I rejected use of services offered by companies based under the jurisdiction of Patriot Act. I use provider within the European Union for binding services to that subdomain.DynDNS. Only necessary ports remain open for public.
-
Hestia has taken a lot of distance from VestaCP and has dramatically enriched security in it.
However, why should a sensitive port should remain accessible and open to 0.0.0.0/24 by default, when this port could be bound to 123.456.123.456 (router dynamic ip address)? Due to binding ports to a specific ip address, there are advantages. Thereafter, ironing vulnerabilities besomes a small issue.
Not binding it and making it remain open to public invites hackers to theaten that port.