Hello!
Last night, around 3 am JST, a server that is using Hestia was automatically upgraded to version 1.8.0 and started presenting err_too_many_redirects errors for websites pointing to it. Before the upgrade, it was working normally.
The server runs on Ubuntu 20.04 LTS.
It hosts a SaaS application that hosts several websites that points to it via CNAME. E.g:
CNAME example.com > saas.example.com
Both websites (example.com and saas.example.com) are using CloudFlare and have their SSL/TLS set to the Full mode, and Always use HTTPS set to ON.
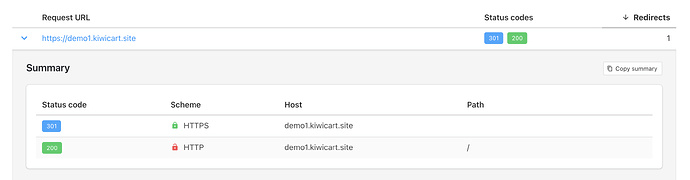
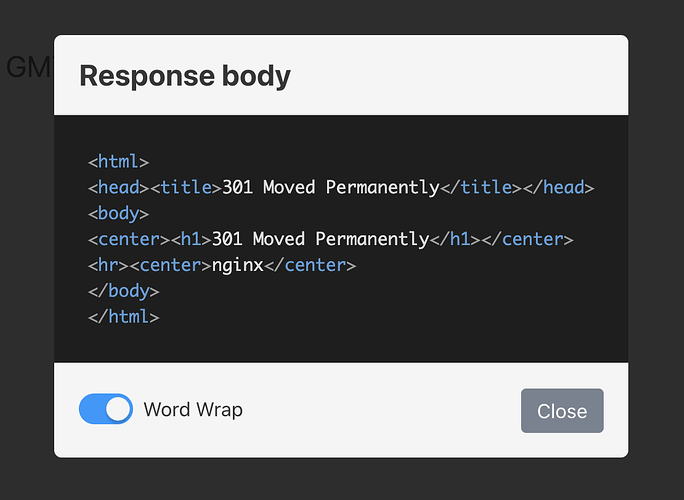
Now, all the websites pointing to the SaaS platform via CNAME are presenting the err_too_many_redirects error.
Usually, Hestia Nginx config listen 8083 ssl is replaced with a custom port number in /usr/local/hestia/nginx/nginx.conf to enable accessing Hestia Panel by a domain name instead of the IP, and always there is an upgrade, Hestia seems to overwrite this file.
However, at this time, it seems that Hestia did not fully updated nginx configuration, and a notification started showing up in Hestia Panel … ![]()
IMPORTANT: Manual Action Required
To enable the 'Enhanced and Optimized TLS' feature, we must update the NGINX configuration file at /etc/nginx/nginx.conf.
But for unknown reason or you edited it, may not be fully apply all the changes in this upgrade.
Please follow the default configuration file to sync it:
/usr/local/hestia/install/deb/nginx/nginx.conf
Backed up configuration file:
/root/hst_backups/120720230322/conf/nginx/nginx.conf
Visit PR #3555 on GitHub to learn more.
I looked into these mentioned files, and it looks like they have changed quite a lot. Some changes are hard to spot, becuase although the instructions are the same, it seems that they have been reordered inside the file along with additional changes …
Given the notification, I’m afraid the issue is related to “Enhanced and Optimized TLS” being disabled.
I’m not experienced with this, so I have no idea where to start!
Would you help me to fix this? ![]()