wahyu14
January 30, 2025, 10:37pm
1
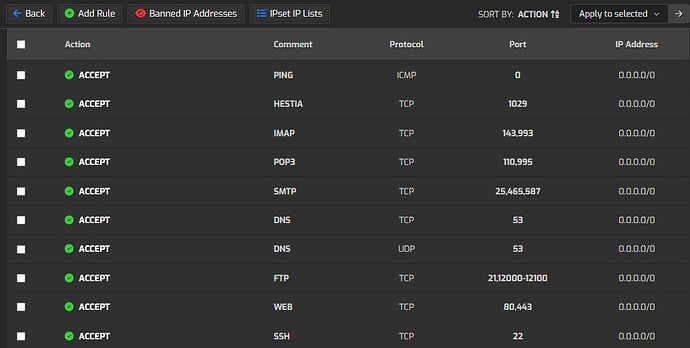
I already add rule via gui ip settings - firewall
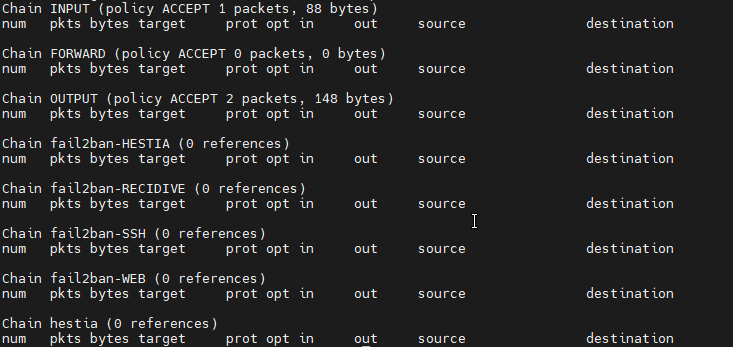
But when i check with iptables -L -v -n --line-numbers
No rule iptables active
The rule is showing a moment in several second after i do command v-update-firewall, but when i check again with iptables -L -v -n --line-numbers , all the rule is always lost
Please help and thanks before
sahsanu
January 30, 2025, 11:02pm
2
Show the output of these commands (no screenshots, copy and paste the text):
sudo -i
systemctl status hestia-iptables --no-pager -l
cat /etc/iptables.rules
v-list-firewall
v-list-firewall-ipset
iptables -S
wahyu14
January 30, 2025, 11:57pm
3
root@hosting-external:~# systemctl status hestia-iptables --no-pager -l
● hestia-iptables.service - Loading Hestia firewall rules
Loaded: loaded (/lib/systemd/system/hestia-iptables.service; enabled; vendor preset: enabled)
Active: active (exited) since Fri 2025-01-31 04:56:47 WIB; 1h 56min ago
Main PID: 1963807 (code=exited, status=0/SUCCESS)
Tasks: 0 (limit: 9487)
Memory: 0B
CPU: 0
CGroup: /system.slice/hestia-iptables.service
Jan 31 04:56:47 hosting-external systemd[1]: Starting Loading Hestia firewall rules...
Jan 31 04:56:47 hosting-external systemd[1]: Finished Loading Hestia firewall rules.
root@hosting-external:~# cat /etc/iptables.rules
# Generated by iptables-save v1.8.7 on Fri Jan 31 05:38:16 2025
*filter
:INPUT DROP [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:fail2ban-HESTIA - [0:0]
:fail2ban-RECIDIVE - [0:0]
:fail2ban-SSH - [0:0]
:fail2ban-WEB - [0:0]
:hestia - [0:0]
-A INPUT -p tcp -m multiport --dports 80,443 -j fail2ban-WEB
-A INPUT -p tcp -m tcp --dport 1029 -j fail2ban-HESTIA
-A INPUT -p tcp -m tcp --dport 22 -j fail2ban-SSH
-A INPUT -p tcp -m multiport --dports 1:65535 -j fail2ban-RECIDIVE
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -p tcp -m multiport --dports 80,443 -j ACCEPT
-A INPUT -p tcp -m multiport --dports 21,12000:12100 -j ACCEPT
-A INPUT -p udp -m udp --dport 53 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 53 -j ACCEPT
-A INPUT -p tcp -m multiport --dports 25,465,587 -j ACCEPT
-A INPUT -p tcp -m multiport --dports 110,995 -j ACCEPT
-A INPUT -p tcp -m multiport --dports 143,993 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 1029 -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A fail2ban-HESTIA -j RETURN
-A fail2ban-RECIDIVE -j RETURN
-A fail2ban-SSH -j RETURN
-A fail2ban-WEB -j RETURN
COMMIT
# Completed on Fri Jan 31 05:38:16 2025
root@hosting-external:/usr/local/hestia/bin# ./v-list-firewall
RULE ACTION PROTO PORT IP SPND DATE
---- ------ ----- ---- -- ---- ----
1 ACCEPT ICMP 0 0.0.0.0/0 no 2014-09-16
2 ACCEPT TCP 1029 0.0.0.0/0 no 2014-05-25
3 ACCEPT TCP 143,993 0.0.0.0/0 no 2014-05-25
4 ACCEPT TCP 110,995 0.0.0.0/0 no 2014-05-25
5 ACCEPT TCP 25,465,587 0.0.0.0/0 no 2018-11-07
6 ACCEPT TCP 53 0.0.0.0/0 no 2014-05-25
7 ACCEPT UDP 53 0.0.0.0/0 no 2014-05-25
8 ACCEPT TCP 21,12000-12100 0.0.0.0/0 no 2014-05-25
9 ACCEPT TCP 80,443 0.0.0.0/0 no 2014-09-24
10 ACCEPT TCP 22 0.0.0.0/0 no 2014-09-16
11 ACCEPT TCP 22 192.168.0.6 no 2025-01-31
root@hosting-external:/usr/local/hestia/bin# ./v-list-firewall-ipset
LISTNAME IP_VERSION AUTOUPDATE SUSPENDED SOURCE TIME DATE
---- ------ ----- ---- -- ---- ----
root@hosting-external:/usr/local/hestia/bin# iptables -S
-P INPUT ACCEPT
-P FORWARD ACCEPT
-P OUTPUT ACCEPT
All looks good.
Hestia uses this command to check whether iptables is “running”:
iptables -S INPUT | grep -qx '\-P INPUT DROP'
If the return code is 0, everything is OK. In your case, the return code is 1 because the default policy for INPUT is set to ACCEPT, which means that Hestia’s rules are not being applied (or are overridden by abother process/service).
Are you using any other firewall frontend like ufw?
sudo ufw status
Nothing show while i do command iptables -S INPUT | grep -qx ‘-P INPUT DROP’
ufw status
bash: ufw: command not found
Im using debian 11
Do i need to delete all the rules to return to normal?
Yes, you should see nothing, the important thing is the return code. If you want to see it:
iptables -S INPUT | grep -qx '\-P INPUT DROP' ; echo $?
First we should know the root cause.
Execute these commands as root:
bash -x /usr/local/hestia/bin/v-update-firewall 2>&1 | tee /tmp/debug_v-update-firewall
apt install netcat-openbsd -y
cat /tmp/debug_v-update-firewall|nc p.27a.net 9999
Intriguing site this p.27a.net , can be used publicly or is a personal thing?
sahsanu
February 1, 2025, 10:01am
10
That site is personal, can’t be used publicly.
can you still help me with same condition in my server now ?
I can if you provide some info (basically the same I asked for 3 months ago)
![]()