OUTPUT OF CMD: iptables -L --line-numbers AFTER REBOOT
# iptables -L --line-numbers
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 fail2ban-HESTIA tcp -- anywhere anywhere tcp dpt:8083
2 fail2ban-MAIL tcp -- anywhere anywhere multiport dports smtp,submissions,submission,pop3,pop3s,imap2,imaps
3 fail2ban-SSH tcp -- anywhere anywhere tcp dpt:63009
4 fail2ban-RECIDIVE tcp -- anywhere anywhere multiport dports tcpmux:65535
5 fail2ban-FTP tcp -- anywhere anywhere tcp dpt:ftp
6 fail2ban-WEB tcp -- anywhere anywhere multiport dports http,https
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
Chain fail2ban-FTP (1 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere
Chain fail2ban-HESTIA (1 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere
Chain fail2ban-MAIL (1 references)
num target prot opt source destination
1 REJECT all -- 94.232.43.50 anywhere reject-with icmp-port-unreachable
2 REJECT all -- airplane.medyamol.com anywhere reject-with icmp-port-unreachable
3 REJECT all -- noiseless.medyamol.com anywhere reject-with icmp-port-unreachable
4 RETURN all -- anywhere anywhere
Chain fail2ban-RECIDIVE (1 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere
Chain fail2ban-SSH (1 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere
Chain fail2ban-WEB (1 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere
OUTPUT AGAIN AFTER: v-update-firewall & iptables -L --line-numbers
# iptables -L --line-numbers
Chain INPUT (policy DROP)
num target prot opt source destination
1 fail2ban-HESTIA tcp -- anywhere anywhere tcp dpt:8083
2 fail2ban-MAIL tcp -- anywhere anywhere multiport dports smtp,submissions,submission,pop3,pop3s,imap2,imaps
3 fail2ban-SSH tcp -- anywhere anywhere tcp dpt:22
4 fail2ban-RECIDIVE tcp -- anywhere anywhere multiport dports tcpmux:65535
5 fail2ban-FTP tcp -- anywhere anywhere tcp dpt:ftp
6 fail2ban-WEB tcp -- anywhere anywhere multiport dports http,https
7 ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
8 ACCEPT all -- dev.evonet.top anywhere
9 ACCEPT all -- localhost anywhere
10 ACCEPT tcp -- anywhere anywhere tcp dpt:webmin
11 DROP tcp -- anywhere anywhere match-set hestia-blacklist-source src
12 ACCEPT udp -- anywhere anywhere udp dpt:https
13 ACCEPT tcp -- anywhere anywhere tcp dpt:22
14 ACCEPT tcp -- anywhere anywhere multiport dports http,https
15 ACCEPT tcp -- anywhere anywhere multiport dports ftp,12000:12100
16 ACCEPT udp -- anywhere anywhere udp dpt:domain
17 ACCEPT tcp -- anywhere anywhere tcp dpt:domain
18 ACCEPT tcp -- anywhere anywhere multiport dports smtp,submissions,submission
19 ACCEPT tcp -- anywhere anywhere multiport dports pop3,pop3s
20 ACCEPT tcp -- anywhere anywhere multiport dports imap2,imaps
21 ACCEPT tcp -- anywhere anywhere tcp dpt:8083
22 ACCEPT icmp -- anywhere anywhere
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
Chain fail2ban-FTP (1 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere
Chain fail2ban-HESTIA (1 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere
Chain fail2ban-MAIL (1 references)
num target prot opt source destination
1 REJECT all -- 94.232.43.50 anywhere reject-with icmp-port-unreachable
2 REJECT all -- airplane.medyamol.com anywhere reject-with icmp-port-unreachable
3 REJECT all -- noiseless.medyamol.com anywhere reject-with icmp-port-unreachable
4 RETURN all -- anywhere anywhere
Chain fail2ban-RECIDIVE (1 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere
Chain fail2ban-SSH (1 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere
Chain fail2ban-WEB (1 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere
Chain hestia (0 references)
num target prot opt source destination
Based on the output, I assume hestia is not keeping the iptable rules correctly after reboot. But I don’t know enough about this…
Please let me know what you think.
Thanks!
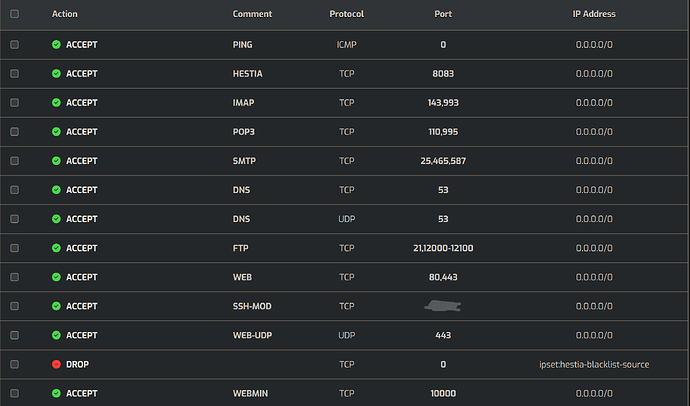
Adding screenshot of hestia gui if helpful