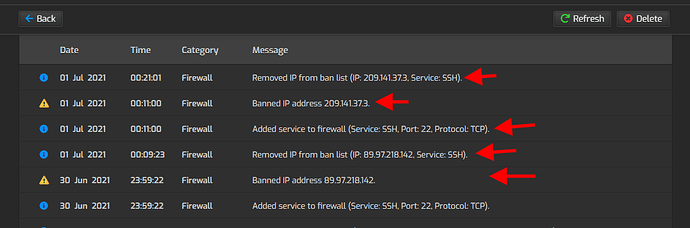
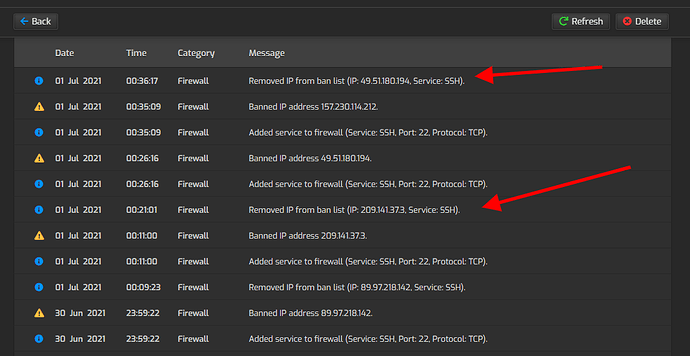
That’s the way fail2ban works.
Imagine that you fail to put your SSH password 3 times. Then you would not be able to ever login again from that IP.
The idea behind fail2ban is to prevent massive attempts to guess your password.
If your password is complicated enough maybe it should need 10.000.000 attempts to be discovered by a hacker. But fail2ban limits the speed to 5 attempts / 10 minutes or 30 attempts / hour.
That would mean 38 years to crack your password.
If you want, you can set a “recidive” jail. The recidive jail bans repeat offenders for much longer period of time. The recidive rule I set is of 10 days for web servers.
For email servers you may need to be mercyful so a misconfigured outlook doesn’t ban an office from the server.
Here is a copy of my jail.local of one of my web servers (I separate email and DNS from web).
Note that some of the jails are experimental.
#este banea intentos de login exitosos
[webexploits-apache]
enabled = false
port = http,https
filter = webexploits
logpath = /var/log/apache2/domains/*.log
maxretry = 3
action = iptables-multiport[name=webexploits, port=“http,https”, protocol=tcp]
findtime = 600
#este no inicia correctamente
[webexploits-nginx]
enabled = false
port = http,https
filter = webexploits
logpath = /var/log/nginx/domains/*.log
maxretry = 3
action = iptables-multiport[name=webexploits, port=“http,https”, protocol=tcp]
findtime = 600
[http-get-dos]
enabled = true
port = http,https
filter = http-get-dos
logpath = /var/log/apache*/*access.log
#Banea 10 minutos a quien hace 300 peticiones en menos de 300 segundos
maxretry = 300
findtime = 300
bantime = 600
action = iptables[name=HTTP, port=http, protocol=tcp]
[ssh-iptables]
enabled = true
filter = sshd
action = hestia[name=SSH]
logpath = /var/log/auth.log
maxretry = 5
[vsftpd-iptables]
enabled = true
filter = vsftpd
action = hestia[name=FTP]
logpath = /var/log/vsftpd.log
maxretry = 5
[exim-iptables]
enabled = true
filter = exim
action = hestia[name=MAIL]
logpath = /var/log/exim4/mainlog
[dovecot-iptables]
enabled = false
filter = dovecot
action = hestia[name=MAIL]
logpath = /var/log/dovecot.log
[mysqld-iptables]
enabled = false
filter = mysqld-auth
action = hestia[name=DB]
logpath = /var/log/mysql.log
maxretry = 5
[hestia-iptables]
enabled = true
filter = hestia
action = hestia[name=HESTIA]
logpath = /var/log/hestia/auth.log
maxretry = 5
[roundcube-auth]
enabled = false
filter = roundcube-auth
action = hestia[name=WEB]
logpath = /var/log/roundcube/errors
maxretry = 5
[recidive]
enabled = true
filter = recidive
action = hestia[name=RECIDIVE]
logpath = /var/log/fail2ban.log
maxretry = 5
findtime = 86400
bantime = 864000