From one last week when I try to change some firewall rules through hestia UI, I get high CPU consumption by v-update-firewall. I need wait sometimes up to 5 minutes to finish update. After firewall rules update i need restart server as plenty ports become closed even they opened by firewall rules. Ubuntu 22 and latest hesta.
Too many ipsets?
v-list-firewall-ipset
Try to debug the command to see where it’s getting stuck.
bash -x /usr/local/hestia/bin/v-update-firewall
root@somefriend:/usr/local/hestia/bin# v-list-firewall-ipset
LISTNAME IP_VERSION AUTOUPDATE SUSPENDED SOURCE TIME DATE
---- ------ ----- ---- -- ---- ----
Its not detect any ip address. In reality I have 3 IPs. One for WAN, one for Inner network, and one for VPN service (WireGuard).
bash -x /usr/local/hestia/bin/v-update-firewall
This is put a lot of outputs in console. As I can see, a lot of repeated and same firewall rules applied.
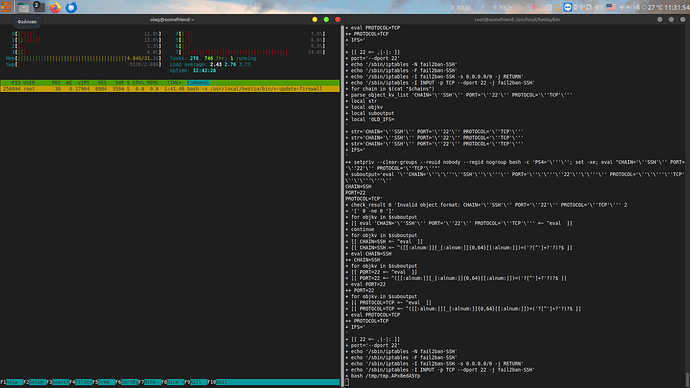
Finally its stacked on this code without exiting from script:
+ [[ 22 =~ ,|-|: ]]
+ port='--dport 22'
+ echo '/sbin/iptables -N fail2ban-SSH'
+ echo '/sbin/iptables -F fail2ban-SSH'
+ echo '/sbin/iptables -I fail2ban-SSH -s 0.0.0.0/0 -j RETURN'
+ echo '/sbin/iptables -I INPUT -p TCP --dport 22 -j fail2ban-SSH'
+ bash /tmp/tmp.APx8edA5Yp
And now I need reboot server full because some ports still closed.
That command won’t show your IP addresses, it shows the IP sets used by iptables… and in this case, you’re not using any IP sets.
So it looks it’s stuck addking chain rules and I would like to see the rules it is trying to add.
I don’t have time now but I’ll try later to modify the script to save the tmp file and check the rules it’s trying to add.
Could you please show the full and unedited output of these commands?
ufw status
iptables -S -t nat
iptables -S
root@somefriend:/# ufw status
Команда «ufw» не найдена, но может быть установлена с помощью:
snap install ufw # version 0.36.2, or
apt install ufw # version 0.36.1-4ubuntu0.1
См. 'snap info ufw', чтобы посмотреть дополнительные версии.
No ufw installed
root@somefriend:/# iptables -S -t nat
-P PREROUTING ACCEPT
-P INPUT ACCEPT
-P OUTPUT ACCEPT
-P POSTROUTING ACCEPT
-A POSTROUTING -o eno1 -j MASQUERADE
-A POSTROUTING -o eno1 -j MASQUERADE
-A POSTROUTING -o eno1 -j MASQUERADE
-A POSTROUTING -o eno1 -j MASQUERADE
root@somefriend:/etc/apache2/conf.d# iptables -S
-P INPUT DROP
-P FORWARD ACCEPT
-P OUTPUT ACCEPT
-N fail2ban-FTP
-N fail2ban-HESTIA
-N fail2ban-MAIL
-N fail2ban-RECIDIVE
-N fail2ban-SSH
-N fail2ban-WEB
-N hestia
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -s 192.168.0.7/32 -j ACCEPT
-A INPUT -s 127.0.0.1/32 -j ACCEPT
-A INPUT -s 10.42.0.0/24 -p icmp -j ACCEPT
-A INPUT -s 10.42.0.0/24 -p udp -m udp --dport 4000 -j ACCEPT
-A INPUT -s 10.42.0.0/24 -p tcp -m tcp --dport 4000 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -p udp -m multiport --dports 3478,5349,49152:65535 -j ACCEPT
-A INPUT -p tcp -m multiport --dports 3478,5349,49152:65535 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 8448 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 9009 -j DROP
-A INPUT -p tcp -m tcp --dport 47777 -j ACCEPT
-A INPUT -p udp -m multiport --dports 67,68 -j ACCEPT
-A INPUT -p tcp -m multiport --dports 67,68 -j ACCEPT
-A INPUT -p tcp -m multiport --dports 80,443 -j ACCEPT
-A INPUT -p tcp -m multiport --dports 21,12000:12100 -j ACCEPT
-A INPUT -p udp -m udp --dport 53 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 53 -j ACCEPT
-A INPUT -p tcp -m multiport --dports 25,465,587 -j ACCEPT
-A INPUT -p tcp -m multiport --dports 110,995 -j ACCEPT
-A INPUT -p tcp -m multiport --dports 143,993 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 8083 -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A FORWARD -i wg0 -j ACCEPT
-A FORWARD -i eno1 -o wg0 -j ACCEPT
-A FORWARD -i wg0 -j ACCEPT
-A FORWARD -i eno1 -o wg0 -j ACCEPT
-A FORWARD -i wg0 -j ACCEPT
-A FORWARD -i eno1 -o wg0 -j ACCEPT
-A FORWARD -i wg0 -j ACCEPT
-A FORWARD -i eno1 -o wg0 -j ACCEPT
-A fail2ban-FTP -j RETURN
-A fail2ban-HESTIA -j RETURN
-A fail2ban-MAIL -j RETURN
-A fail2ban-RECIDIVE -j RETURN
-A fail2ban-SSH -j RETURN
-A fail2ban-WEB -j RETURN
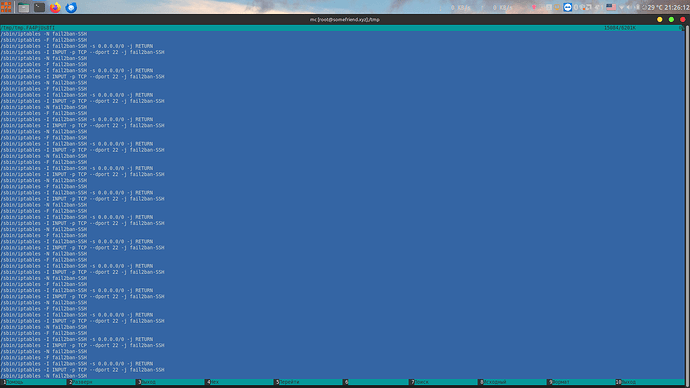
I check /tmp/tmp.APx8edA5Yp file what created by v-firewall-update and found 6 millions of lines. And of course all this lines is doubled.
Ok, there is something wrong in chains conf. Show the output of this command:
cat -A /usr/local/hestia/data/firewall/chains.conf
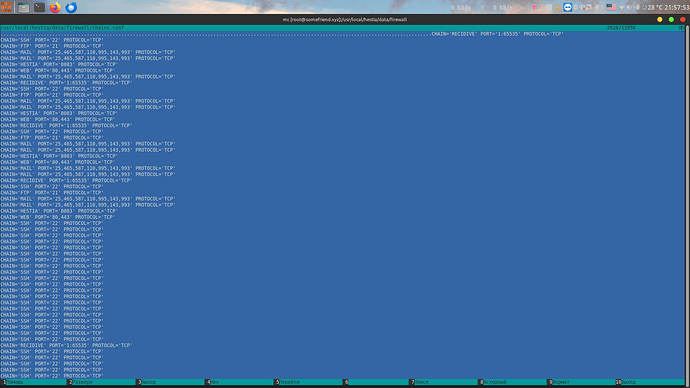
I use sort chains.conf | uniq to bring config to normal condition.
Now content of chains.conf is:
CHAIN='RECIDIVE' PORT='1:65535' PROTOCOL='TCP'
CHAIN='FTP' PORT='21' PROTOCOL='TCP'
CHAIN='HESTIA' PORT='8083' PROTOCOL='TCP'
CHAIN='MAIL' PORT='25,465,587,110,995,143,993' PROTOCOL='TCP'
CHAIN='SSH' PORT='22' PROTOCOL='TCP'
CHAIN='WEB' PORT='80,443' PROTOCOL='TCP'
Now only 30 seconds keep firewall update and ports are properly opened.
Any idea why chains.conf has so many doubled lines?
Ok.
Great!
No.
This topic was automatically closed 30 days after the last reply. New replies are no longer allowed.