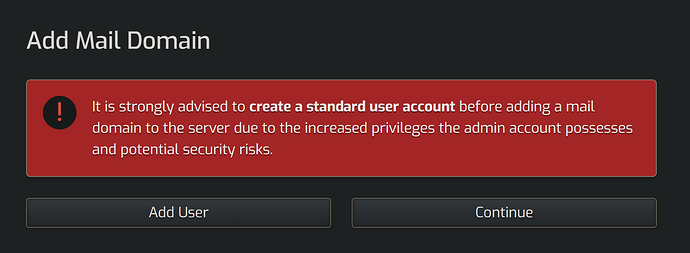
I’m curious about the specifics of this message. Thanks!
Create a php script with
<?php exec('sudo /usr/local/hestia/bin/v-change-user-password admin "newpassword" And upload it to /home/admin/web/domain.com/public_html And access via web Enough said...Thanks for the info @eris
You are saying if php exec is enabled (which is a security risk in and of itself), if someone is somehow able to upload a php script, they can access all the hestia commands.
Say security-risk php commands like exec, passthru, shell_exec, system, proc_open, popen, curl_exec, curl_multi_exec, parse_ini_file, show_source, etc are disabled at the master php level…
other security risk examples…?
Also, hestia creates a the hostname website publicly exposed to the internet. How is that not the same security risk you initially mentioned?
Thanks!
Because I don’t put a website on my hostname and we assume nobody does… If they do they should really move it to a different user.
But that is up to them.
Anyway we will change this behaviour in a future update anyways …
Is this needed to issue SSL cert or for any other reason i.e. is it fine to delete hostname website?
Any additional thoughts? Or only access to all cli commands for admin user?
Hostname can be under any user it really don’t matter how ever it is written so it creates under the admin user if it doesn’t exists…
There might be other security vulnerabilities to be found that gives shell access to the user running php / apache2 or nginx so that is why it always run any user with limited permissions…
It will be replaced anyway in the next major release… As we found that nobody cares about it and ignores the warning anyways… I was an design choice in VestaCP and we carried it over when we forked it but it was a bad decision to start with…
Thanks for the additional info.
Is a hostname web domain needed to issue SSL cert or for any other reason? Or is it fine to delete it?
Following up @eris
And thanks for answering my questions about these details. I’m creating unattended hestia server provisioning with ansible.
Thanks @eris
SOLUTION:
Create a php script with
<?php exec('sudo /usr/local/hestia/bin/v-change-user-password admin "newpassword" And upload it to /home/admin/web/domain.com/public_html And access via web Enough said...
AND RE: HOSTNAME
Because I don’t put a website on my hostname and we assume nobody does… If they do they should really move it to a different user.
AND RE: HOSTNAME + OTHER SECURITY ISSUES
Hostname can be under any user it really don’t matter how ever it is written so it creates under the admin user if it doesn’t exists…
There might be other security vulnerabilities to be found that gives shell access to the user running php / apache2 or nginx so that is why it always run any user with limited permissions…
It will be replaced anyway in the next major release…
AND SOULTION RE: HOSTNAME: FROM:
Is hestia created hostname web domain needed to issue SSL cert or for any other reason? Or is it fine to delete it? Thanks!
This topic was automatically closed 30 days after the last reply. New replies are no longer allowed.