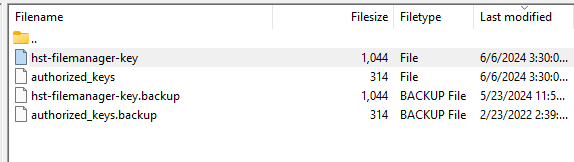
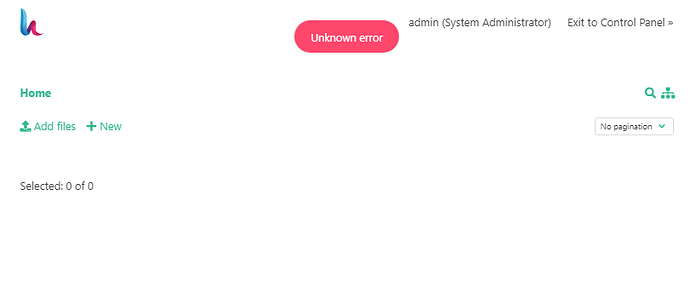
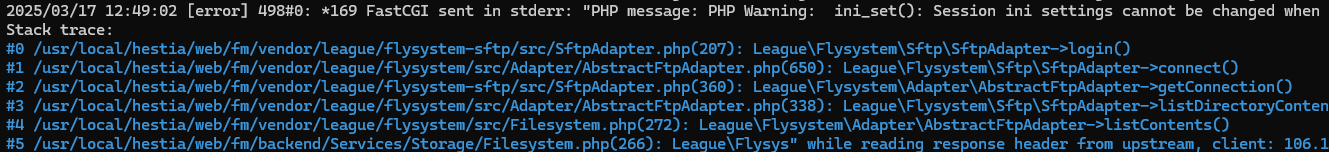
Hi good day to you Sir, please find the screenshot, when I delete the hst-filemanager-key, it automatically create new one, and tried on our hcp, still the same.
Check the /var/log/hestia/nginx-error.log as root user
If you don’t have root access ask the person who has it
Yes logged as root user, kindly check when I open the file it is empty.
Check in this case nginx-error.log.1
Probally just rolled over to create a new one
I saw bunch of logs, which log I should check? Thank you
Check now the log file and check what the error is…
Please check Sir.
Thanks
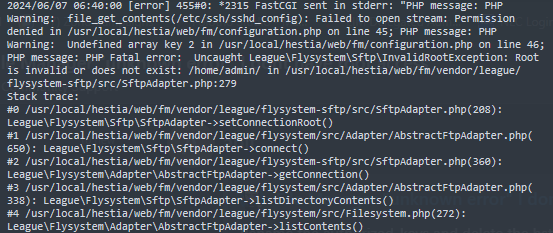
Usually, the default port of SSH is not 22, or the configuration does not enable folder permissions! You can use the following command to view it!
grep -riE 'sftp|AllowUsers|Authentication|UsePAM|Port' /etc/ssh/sshd_config /etc/ssh/sshd_config.d/
There will be the following output (line 17)
/etc/ssh/sshd_config:Port 2974
/etc/ssh/sshd_config:# Authentication:
/etc/ssh/sshd_config:#HostbasedAuthentication no
/etc/ssh/sshd_config:# HostbasedAuthentication
/etc/ssh/sshd_config:ChallengeResponseAuthentication no
/etc/ssh/sshd_config:#KerberosAuthentication no
/etc/ssh/sshd_config:#GSSAPIAuthentication no
/etc/ssh/sshd_config:# Set this to 'yes' to enable PAM authentication, account processing,
/etc/ssh/sshd_config:# and session processing. If this is enabled, PAM authentication will
/etc/ssh/sshd_config:# be allowed through the ChallengeResponseAuthentication and
/etc/ssh/sshd_config:# PAM authentication via ChallengeResponseAuthentication may bypass
/etc/ssh/sshd_config:# and ChallengeResponseAuthentication to 'no'.
/etc/ssh/sshd_config:UsePAM yes
/etc/ssh/sshd_config:GatewayPorts no
/etc/ssh/sshd_config:Subsystem sftp internal-sftp
/etc/ssh/sshd_config:PasswordAuthentication yes
/etc/ssh/sshd_config:PubkeyAuthentication no
/etc/ssh/sshd_config:# Hestia SFTP Chroot
/etc/ssh/sshd_config:Match User sftp_dummy99,admin,www
/etc/ssh/sshd_config: ForceCommand internal-sftp
For example, if the ‘PubkeyAuthentication’ field is ‘no’, you can edit the ‘sshd’ configuration file
nano /etc/ssh/sshd_config
The ‘PubkeyAuthentication no’ field in the configuration file is ‘PubkeyAuthentication yes’ and save!
It can also be modified with one click using the ‘sed’ command
sed -i 's/^PubkeyAuthentication no/PubkeyAuthentication yes/' /etc/ssh/sshd_config
Check whether the modification is successful
grep -riE 'sftp|AllowUsers|Authentication|UsePAM|Port' /etc/ssh/sshd_config /etc/ssh/sshd_config.d/
There will be the following output (line 17)
/etc/ssh/sshd_config:Port 2974
/etc/ssh/sshd_config:# Authentication:
/etc/ssh/sshd_config:#HostbasedAuthentication no
/etc/ssh/sshd_config:# HostbasedAuthentication
/etc/ssh/sshd_config:ChallengeResponseAuthentication no
/etc/ssh/sshd_config:#KerberosAuthentication no
/etc/ssh/sshd_config:#GSSAPIAuthentication no
/etc/ssh/sshd_config:# Set this to 'yes' to enable PAM authentication, account processing,
/etc/ssh/sshd_config:# and session processing. If this is enabled, PAM authentication will
/etc/ssh/sshd_config:# be allowed through the ChallengeResponseAuthentication and
/etc/ssh/sshd_config:# PAM authentication via ChallengeResponseAuthentication may bypass
/etc/ssh/sshd_config:# and ChallengeResponseAuthentication to 'no'.
/etc/ssh/sshd_config:UsePAM yes
/etc/ssh/sshd_config:GatewayPorts no
/etc/ssh/sshd_config:Subsystem sftp internal-sftp
/etc/ssh/sshd_config:PasswordAuthentication yes
/etc/ssh/sshd_config:PubkeyAuthentication yes
/etc/ssh/sshd_config:# Hestia SFTP Chroot
/etc/ssh/sshd_config:Match User sftp_dummy99,admin,www
/etc/ssh/sshd_config: ForceCommand internal-sftp
Use this command to restart the ‘sshd’ configuration
systemctl restart sshd
Then log in to the ‘WEB’ interface of the ‘Hestia’ panel, go to the file manager, and you’ll be amazed to see that no errors are displayed!
I encountered this issue after the 1.9.1 update, I need to do this to all the users to make it work.
Works now, Hope this helps for the next patch
Same here
I can’t access with admin user but all other users i can access the filemanager. Have tried all the solutions from the forum but none of them solved my case. A solution must appreciated, thanks.